
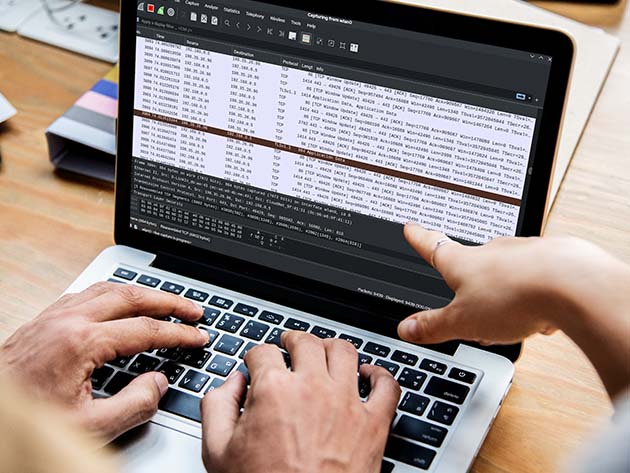
KEY FEATURES
Learn Wireshark practically. Wireshark pcapng files provided so you can practice while you learn! The course is very practical. You can practice while you learn! Learn how to analyze and interpret network protocols and leverage Wireshark for what it was originally intended: Deep Packet Inspection and network analysis. This course will show you have to hack network protocols using Kali Linux! Hack network protocols like DTP, VTP, STP, and DHCP using Ethical hacking tools included in Kali Linux.
- Access 204 lectures & 13 hours of content 24/7
- Troubleshoot networks using Wireshark
- Capture VoIP, OSPF, HTTP, Telnet, & many other protocols using Wireshark
- Learn how to use Wireshark for Ethical hacking
- Improve your job prospects by adding Wireshark to your resumé
- Understand & interpret network protocols.
- Hack network protocols using Kali Linux
PRODUCT SPECS
Important Details
- Length of time users can access this course: lifetime
- Access options: desktop & mobile
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: beginner
- Have questions on how digital purchases work? Learn more here
Requirements
- Any device with basic specifications
THE EXPERT
David Bombal | CCIE #11023 Emeritus, Over 15 Years of Network Training ExperienceDavid Bombal passed his Cisco Certified Internetwork Expert Routing and Switching exam in January 2003 and is one of a small percentage of Cisco Engineers that pass their CCIE labs on their first attempt. David qualified as a Cisco Certified Systems Instructor (CCSI #22787) many years ago! He has been training Cisco courses for over 15 years and has delivered instructor-led courses in various countries around the world covering a wide range of Cisco topics from CCNA to CCIE. David is very active on social media and has over 250,000 YouTube subscribers and has posted over 1,000 free videos.

KEY FEATURES
Networks are all around us and you are using one right now to access this course. The Internet is extremely important in modern life today and this reliance is only predicted to continue with the growth of the Internet of Things (IoT) in the next few years. This course will teach you how networks actually work and how you are able to connect to websites like Facebook, Google, and YouTube. Companies throughout the world (from the smallest to the largest) rely on networks designed, installed, and maintained by networking engineers. Aside from the practical knowledge, this course preps you for the newest CCNA 200-301 exam. This is your first step towards attaining your Cisco certifications.
- Access 738 lectures & 77 hours of content 24/7
- Learn how to configure Cisco Routers & Switches
- Understand how Kali Linux can be used to hack networks
- Explore topics such as Wi-Fi, Network Automation & Network Security
- Apply what you've learned to real-world networking scenarios
- Prepare for the CCNA 200-301 certification exam
IMPORTANT: This course is created for educational purposes and all the information learned should be used when the attacker is authorized.
PRODUCT SPECS
Important Details
- Length of time users can access this course: lifetime
- Access options: desktop & mobile
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: beginner
- Have questions on how digital purchases work? Learn more here
Requirements
- Any device with basic specifications
THE EXPERT
David Bombal | CCIE #11023 Emeritus, Over 15 Years of Network Training ExperienceDavid Bombal passed his Cisco Certified Internetwork Expert Routing and Switching exam in January 2003 and is one of a small percentage of Cisco Engineers that pass their CCIE labs on their first attempt. David qualified as a Cisco Certified Systems Instructor (CCSI #22787) many years ago! He has been training Cisco courses for over 15 years and has delivered instructor-led courses in various countries around the world covering a wide range of Cisco topics from CCNA to CCIE. David is very active on social media and has over 250,000 YouTube subscribers and has posted over 1,000 free videos.

KEY FEATURES
Most of the data are now accessed via web applications, mobile, and APIs. As of today, more than 75% of the attacks are in the wild target web. Bug bounty is also focused more on web since the apps are more prone to security bugs compared with an infrastructure device. This training is based on a practical approach to day-by-day situations and it contains labs based on real environments. For the labs, target virtual machines are provided. The course objective is to help you learn to master the (ethical) hacking techniques and methodology that are used in penetration systems. This course covers both theoretical and practical aspects and contains hands-on labs about hacking systems, networks, wireless, mobile, and websites.
- Access 71 lectures & 9 hours of content 24/7
- Get an overview of ethical hacking, footprinting, & reconnaissance
- Learn sniffing, attacking authentication, & session management
- Exploit SQLi using SQLmap & getting remote shell
- Play with Android emulators & practice your social engineering
PRODUCT SPECS
Important Details
- Length of time users can access this course: lifetime
- Access options: desktop & mobile
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
- Have questions on how digital purchases work? Learn more here
Requirements
- Any device with basic specifications
THE EXPERT
Gabriel Avramescu | Senior Information Security Consultant | IT TrainerGabriel Avramescu works on the Internet security team, focused on ethical hacking - deliberately and purposefully challenging the IT security assumptions, strategies, and methods of protecting vital assets and information by emulating an adversary. He acts as an effective participant on a multidisciplinary security project team.

KEY FEATURES
Lots of people are focusing on web security, but they many don't have enough knowledge to find and exploit vulnerabilities when it comes to infrastructure. Since bug bounty is a competition, every additional knowledge helps. This training is based on a practical approach to day-by-day situations and it contains labs based on real environments. For the labs, target virtual machines are provided. This course covers both theoretical and practical aspects and contains hands-on labs about hacking systems, networks, wireless, mobile, and websites.
- Access 50 lectures & 5 hours of content 24/7
- Scan networks, enumeration, & discover vulnerabilities
- Use SET to get Facebook credentials
- Learn system hacking & vulnerability exploitation
- Exploit FTP server vulnerability using Metasploit
- Know about trojans, backdoors, viruses, & worms
- Do penetration testing on wireless networks
PRODUCT SPECS
Important Details
- Length of time users can access this course: lifetime
- Access options: desktop & mobile
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
- Have questions on how digital purchases work? Learn more here
Requirements
- Any device with basic specifications
THE EXPERT
Gabriel Avramescu | Senior Information Security Consultant | IT TrainerGabriel Avramescu works on the Internet security team, focused on ethical hacking - deliberately and purposefully challenging the IT security assumptions, strategies, and methods of protecting vital assets and information by emulating an adversary. He acts as an effective participant on a multidisciplinary security project team.
KEY FEATURES
This practical, hands-on course was created for newbies – that's to say, people with no prior training or knowledge in hacking and cybersecurity. The aim of this course is to give you the education not just to understand what black-hat hatters do and how, but also to learn exactly how to hack systems like a pro and win the cat and mouse game by securing systems like a professional security expert. This approach gives you the foundational education that you need not just to hack any given system, but also to secure it, with each module covering both sides of the coin.
- Access 104 lectures & 12 hours of content 24/7
- Set up a hacking lab
- Launch attacks/exploits against computers
- Start a cybersecurity/ethical hacking career
- Hack into wireless networks
- Conduct penetration tests
- Bypass antivirus
- Learn the fundamentals of networking, Linux, Bash, & more
PRODUCT SPECS
Important Details
- Length of time users can access this course: lifetime
- Access options: desktop & mobile
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
- Have questions on how digital purchases work? Learn more here
Requirements
- Any device with basic specifications
THE EXPERT
Juan Galvan | Digital Entrepreneur | Marketer | VisionaryJuan Galvan has been an Entrepreneur since grade school. He has started several companies, created many products, and sold on various online marketplaces with great success. He founded Sezmi SEO, an agency based out of Seattle, Washington. His collection of principles, thoughts, and sayings has grown over the years. These have come from the teachings of powerful and famous people like Warren Buffett, Charlie Munger, Peter Drucker, Jim Rohn, and his mentors.

KEY FEATURES
To be able to perform successful penetration testing or ethical hacking. First, you have to know all the secrets of your targets. You should find all the systems and network devices of your target network before proceeding with an ethical hacking operation. In this course, you`ll discover the secrets of ethical hacking and network discovery using Nmap. You’ll learn all the Nmap details, which is the most known and de facto network scanning tool. Then in further lessons, you’ll scan the vulnerabilities of the network you discovered by using Nessus. Nessus is the most known vulnerability scanner and is in the third place of the most popular cybersecurity tools.
- Access 59 lectures & 4 hours of content 24/7
- Understand the main terminology of Network Scanning & Finding Vulnerabilities in devices in a network
- Use Nmap with full knowledge & experience
- Scan a network for scripts
- Learn about networking scan types
- Learn how to use Hping
PRODUCT SPECS
Important Details
- Length of time users can access this course: lifetime
- Access options: desktop & mobile
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
- Have questions on how digital purchases work? Learn more here
Requirements
- Any device with basic specifications
THE EXPERT
Oak Academy | Long Live Tech KnowledgeOak Academy is a group of tech experts who have been in the sector for years and years. Deeply rooted in the tech world, they know that the tech industry's biggest problem is the "tech skills gap" and their online course is their solution. They specialize in critical areas like cybersecurity, coding, IT, game development, app monetization, and mobile. Thanks to their practical alignment, they are able to constantly translate industry insights into the most in-demand and up-to-date courses.

KEY FEATURES
The CompTIA Network+ Certification is a trusted mid-level certification for network technicians. Network+ professionals possess well-grounded knowledge and skills in troubleshooting, configuring, and managing networks. With 21 hours of instruction, this course aims to make you a good Network Tech and, in the process, make sure you are ready to pass the CompTIA exam.
- Access 168 lectures & 21 hours of content 24/7
- Design & implement functional networks
- Understand & execute network security, standards, and protocols
- Troubleshoot basic to advanced network problems
IMPORTANT: This course is created for educational purposes and all the information learned should be used when the attacker is authorized.
PRODUCT SPECS
Important Details
- Length of time users can access this course: lifetime
- Access options: desktop & mobile
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: intermediate
- Have questions on how digital purchases work? Learn more here
Requirements
- Basic familiarity with networks
THE EXPERT
Total Seminars | Home of Mike Meyers & His Team of IT Certification ProsTotal Seminars provides certification training services and training materials to thousands of schools, corporations, and government agencies including the United Nations, the FBI, and all branches of the Department of Defense. Total Seminars produces the #1 selling CompTIA A+ and Network+ Certification books with over 1 million books in print.
Total Seminars has created a number of “Best-Selling” Udemy video courses by Mike Meyers and the Total Seminars team of Instructors. They also develop supplemental materials such as the TotalTester certification practice tests and TotalSims lab simulations to support your certification preparation. These are available on the Total Seminars website.

KEY FEATURES
This course covers everything you need to know to pass your CompTIA Security+ (SY0-601) certification exam. With over 17 hours of in-depth and fascinating content and 125 video lectures, this course will not only make you a good IT security tech but make sure you are ready to pass the CompTIA Security+ exam. Your new skills and the CompTIA Security+ Cert will help you land a great IT security tech job or, get that raise or advancement you are after.
- Access 122 lectures & 17 hours of content 24/7
- Apply the three “A’s” of security: authentication, authorization, & accounting
- Scan your wired or wireless network and assess it for various weaknesses
- Use cryptography to assure the integrity of data through hashing & confidentiality of data through symmetric/asymmetric cryptosystems and public key infrastructure (PKI)
- Understand critical concepts in risk management, like setting up alerts, responding to incidents, & mitigating vulnerabilities
- Identify how hackers are trying to get into your network, IT infrastructure, & physical assets and how security techs help prevent those breaches
- Prevent attacks ranging from simple malware to sophisticated exploits to social engineering that takes advantage of people’s trust, relationships, & lack of knowledge
- Apply the techniques used in penetration testing, including passive & active reconnaissance
- Secure an enterprise environment, including creating an incident response, business continuity, & disaster recovery plans
IMPORTANT: This course is created for educational purposes and all the information learned should be used when the attacker is authorized.
PRODUCT SPECS
Important Details
- Length of time users can access this course: lifetime
- Access options: desktop & mobile
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: intermediate
- Have questions on how digital purchases work? Learn more here
Requirements
- Basic familiarity with networks
THE EXPERT
Total Seminars | Home of Mike Meyers & His Team of IT Certification ProsTotal Seminars provides certification training services and training materials to thousands of schools, corporations, and government agencies including the United Nations, the FBI, and all branches of the Department of Defense. Total Seminars produces the #1 selling CompTIA A+ and Network+ Certification books with over 1 million books in print.
Total Seminars has created a number of “Best-Selling” Udemy video courses by Mike Meyers and the Total Seminars team of Instructors. They also develop supplemental materials such as the TotalTester certification practice tests and TotalSims lab simulations to support your certification preparation. These are available on the Total Seminars website.

KEY FEATURES
This course will guide you through creating a fully-functional and smart security camera, using a Raspberry Pi or the webcam on your device. The purpose of the application in this course is to detect movement in the video footage and subsequently execute an action, such as sending out an email or an SMS. Sections covering both the theory and practical applications are included in this course. The theory videos demonstrate the building blocks so that you can understand how it all works. Topics taught in this course include summation notation, image similarity metrics, and video processing. Image similarity is a set of tools that we can use to compare images, which then helps us determine how similar they are.
- Access 22 lectures & 2 hours of content 24/7
- Create a fully-functional and smart security camera, using a Raspberry Pi or the webcam on your device
- Detect movement in the video footage & subsequently execute an action
- Learn about summation notation, image similarity metrics, & video processing
PRODUCT SPECS
Important Details
- Length of time users can access this course: lifetime
- Access options: desktop & mobile
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: beginner
- Have questions on how digital purchases work? Learn more here
Requirements
- Any device with basic specifications
THE EXPERT
Zenva AcademyTrusted by 400,000+ learners and developers, Zenva provides world-class training on in-demand programming skills covering game development, machine learning, virtual reality, and full-stack web development. The e-learning platform Zenva Academy is the leading place to upskill, learn and gain key tech skills for the innovation economy.
